Managing Risk and Automation in a Multi-Cloud World with Policy as Code
Enterprise organizations today face a daunting array of challenges in their quest to deliver optimally secure IT services that comply with corporate and government mandates. Addressing such challenges has never been a trivial affair. Indeed, over the past decade and more, as technology stacks and platforms have increased in their heterogeneity and complexity, meeting the demands of effective risk governance has only become more difficult.
As is the case with much of enterprise management, the challenge here isn’t typically a matter of inadequate tools or technology. More often, it’s one of human systems, processes, culture, and organization. A polling of ONUG Collaborative members confirms this. We know, for example, that the practice of transforming a set of security requirements into code, just as enterprises have increasingly done with infrastructure in recent years, allows us to test operational frameworks and configurations against that code to determine the extent of policy compliance in a given setting. We know that such testing can be embedded in service delivery pipelines and automated accordingly – and that the potential of this approach, smartly implemented, is for both higher quality and faster cadence time-to-market deployments. Finally, we know that both Cloud Service Providers and independent third-party vendors alike provide well-developed products and services for implementing such “Policy as Code” solutions. But this is where our certainty currently ends.
What Is Policy as Code (PaC)
Policy as code formalizes business intent into code, creating intent-driven software that can be evaluated across multiple cloud providers and on-prem systems. Such code allows for enforcing policies across and within the infrastructure, providing appropriate compliance guidelines and guardrails. Policy as code is foundational to the design and delivery of an automated continuous control framework. Policy as code puts control directly in the hands of the business consumer versus the IT/Cloud Service Provider supplier.
As Collaborative members have pointed out, beyond these broad strokes, there is very little in terms of industry operational guidance or standards for us to follow as we look to construct more robust approaches to developing and enforcing policy governance. The following, for instance, are some of the questions that come to mind in this area:
- What would constitute an effective set of guidelines for translating high-level business requirements around risk into specific policies?
- How might we ensure that those higher level policy articulations ramify through to lower-level architectures?
- What policy languages should one employ? Indeed, what should be the criteria for language selection? Or, do we need to define a new, common language?
- And for that matter, do we also need a common, broad-based, multi-tiered “Policy as Code reference architecture”?
- How will the integrity, confidentiality, and availability of policies and policy state be verified?
- How will policies be managed by identity authentication systems and domain-specific toolchains responsible for policy enforcement?
- How can policy as code be used to reduce toil and improve transparency for second line functions?
- Does the recent work of the CNCF in this area, namely their Open Policy Agent initiative, meet the needs of industry practitioners?
- Once expressed in software, moreover, how does one proceed to manage the policy codebase so as to maintain consistency of intent and avoid the problems of “drift”?
- Wouldn’t Policy as Code playbooks serve a useful purpose as enterprises pursue new policy governance strategies?
The challenge is clear: how to move from the initial statement of intent to verification of compliance, reliably and repeatedly? Scratch the surface on this topic, and such questions and concerns are but the beginning of the conversation that results.
Clearly, Policy as Code is seen within the Collaborative as holding significant potential for advancing the automated governance of risk in both private, on-premises and public Cloud settings. And yet it’s also recognized that this potential remains largely unmet. Collaborative members have suggested the subject requires focused attention and leadership, and that for Policy as Code to become an effective tool in enterprise governance, we will need to develop a “well-defined Policy as Code framework,” as one of our Collaborative members put it. As another leader in the group noted, the need is for a “standard approach” to operationalizing Policy as Code – one where all terms are crisply defined – and with clear guardrails articulated. Across the board, the sense was indicated that such an initiative would be of strategic value to the ONUG Community.
The ONUG Collaborative Policy as Code Working Group Initiative
In response to the Collaborative’s interest in this subject, first indicated in the ONUG Spring Conference 2022 voting round and subsequently reinforced at the last Collaborative Steering Committee meeting, ONUG will establish a new ONUG Working Group that will seek to develop and promote Policy as Code as a better-defined and effective means for achieving risk governance and automation within multi-cloud environments.
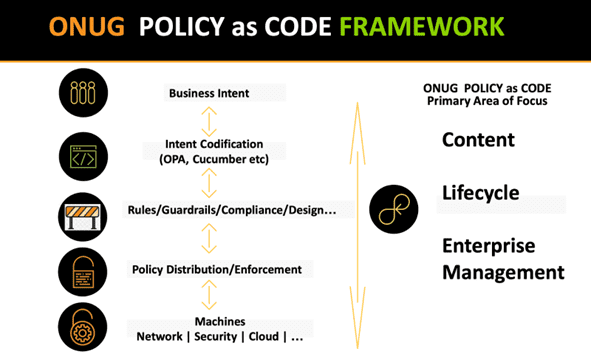
The following image shows the Policy as Code space and ONUG’s suggested area of focus:
We Welcome Your Participation
There are a group of companies that will be participating in this working group including BofA, Citi, Fidelity, FedEx, Cigna, Raytheon, and suppliers Cisco, Microsoft Azure, IBM Cloud, and Oracle Cloud. If managing risk and automation in a multi-cloud world with policy as code is important to you and your organization, then we welcome you to participate in this working group especially as we focus on scope. You can sign up here.
We will start with defining the vocabulary of Policy as Code (PaC) so the industry speaks the same language. Every IT group views PaC differently–some as a means to segment a network, others as a firewall to allow or deny access to resources, and others still as an audit and compliance tool. This phase of work will manifest in the form of a framework documented and published as a Creative Commons open source paper. The first use cases will be in the networking space to prove the framework before we move on to other areas of multi-cloud infrastructure. The desired working group outcome will be a range of solutions that consumers can purchase to gain control over their infrastructure so that it adheres to business initiatives and priorities.
The first PaC Working Group meeting is being scheduled for mid August. Over the next several weeks, we will populate leadership positions within the working group such as co-chairs, project leaders, and advocators. To take on a leadership position, first, sign up for the working group and get on the distribution list; just go here: https://onug.net/collaborative-application/


