
Is Your Multi-Cloud Estate Secure?
It is unlikely that anyone would question the need for securing their hybrid multi-cloud estate; the number of mission-critical applications running in the public cloud nearly doubled between 2020 and 2021, and the growth is expected to continue. (Source: 451 Research’s Voice of the Enterprise: Information Security, Budgets & Outlook 2021). Cloud providers want to mitigate concerns, often saying, “The cloud is more secure than your on-prem network.” This is true, sort of.
Public cloud providers have more highly trained experts focused on cloud security than most enterprise IT shops have on staff. It can be reassuring to know that they have so many highly skilled people protecting your cloud traffic. But what are they committed to securing? It depends on what services you are purchasing. The shared responsibility created by AWS and embraced by all public cloud providers means you’re still responsible for protecting your data and access at the very least and potentially much more (See Figure 1). Before determining if your hybrid multi-cloud estate is secure, you must understand what you’re responsible for securing, then you can take measure of your estate.
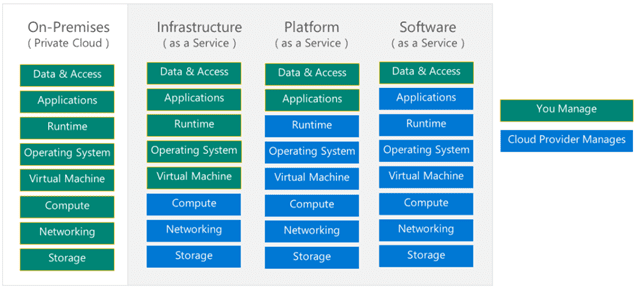
Figure 1: Cloud Provider Shared Responsibility Model
How do you know if your cloud is secure?
Once you’ve determined your responsibilities, the challenging work starts. Most mature enterprises have extensive security policies for their on-premises estate and a technology stack dedicated to ensuring compliance. But it’s not as simple as just “extending” these policies to the cloud. Traditional security controls are ineffective in the cloud since defensible perimeters are erased, component virtualization and decentralization obscures visibility, and automated configuration tools are required at scale.
Cloud providers do not make it easy for you. Not only is cloud topology represented much differently than on-prem, but each cloud provider has its own nomenclature, methodology, visualization, and toolset (See Figures 2 and 3).
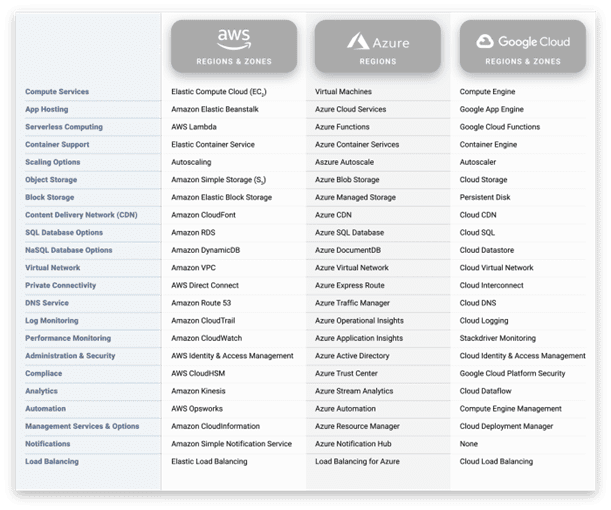
Figure 2: Cloud providers have proprietary nomenclature
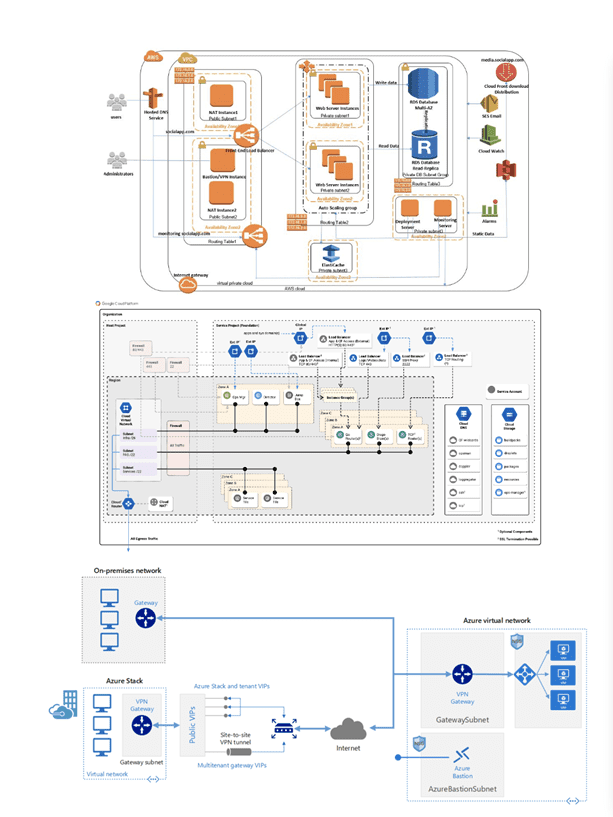
Figure 3: Cloud providers’ visual representation of their environments are proprietary
What is needed to ensure hybrid multi-cloud compliance?
The first step to ensuring compliance is breaking through the complexity. Most enterprises have detailed diagrams of their estate, Teams need a normalized and detailed yet consumable way to visualize the cloud estate alongside the on-premises environment in a single view.
Many organizations are turning to CSPM (Cloud Security Posture Management) to help secure their virtual estate. But even the best CSPM solutions have limits, including presenting data in difficult to interpret static formats and obscuring relationships between resources, such as between multiple accounts and whether they’re shared or not. CSPM tools can show connectivity where there is traffic, but security teams need to understand possible paths to the Internet, the security points traffic would pass through, including ports and protocols.
Another challenge with existing third-party cloud security tools, they don’t always detect all security controls, which means they can report the network is compliant when it’s not. This is even more likely to occur in multi-cloud environments.
This is not to say these tools are not valuable, but that they need to be augmented. Teams need a dynamic, searchable, simplified way of visualizing end-to-end traffic flows (and possible flows). It is important that operators are alerted in a timely manner when changes are made that violate policy (according to Gartner 99% of cloud security breaches will be caused by human error through 2023) and provided the information they need to remediate the exposure. It’s also important to understand the history of the estate for audit responses and forensic investigations should the need arise.
Enterprises should focus on the following areas to ensure multi-cloud compliance:
Visibility. The first step for enterprise IT will be gaining visibility into the use of cloud services – the functions that are used – whether from the cloud service or from a third party, and how applications are configured and deployed. This data must be collected from live environments to independently ensure that the application is configured and operating as intended.
Rationalizing. Next, IT will have to rationalize the security, monitoring and availability controls across each service and product to ensure that the applications and clouds are conformant to IT and the business goals. Data collection will have to be automated and real-time to keep up with changes to applications and infrastructure and ensure that cloud applications remain compliant.
Auditing. Once cloud and application configuration data is collected and processed, it can be used to monitor changes and flag potential issues as they arise across all environments before there’s a headline.
Verifying data flow. Network-based applications should be operated with strict access controls applied so that only authorized application components can use them. Active, real-time monitoring will be the key to proper management.
To learn more, please join me at Center415 on 5th Avenue for ONUG Fall on October 19 at 3:20m ET when I will be speaking about “Verifying Security Posture in Hybrid Multi-Cloud Environments.” Hope to see you there!



